
AMD recently revealed some details about the vulnerability of its CPUs based on all versions of the Zen architecture, including the extremely popular Ryzen 1000, 2000, 4000, 5000 and Ryzen 7000 chips, as well as Ryzen Threadripper workstation CPUs and EPYC server CPUs.
Without going into details, Inception allows stealing data by making the processor “mislead”. The chip “thinks” that it is executing the same function over and over again, so it redirects it to the branch prediction module. Thus, thanks to an extremely simple function, a hacker can gain access to data stored in CPU memory.
Phoronix resource has released a large-scale performance research of AMD patch for Inception vulnerability. The basis of the enthusiasts’ test bench was a 64-core EPYC 7763 (Zen 3/DDR4) chip. Be sure to check out the full article on the topic, while we’ll just briefly run through the main benchmarks and draw isolated conclusions.
First, let’s take a look at the CPU test modes:
- off – No Inception mitigations. All other CPU security mitigations were at their defaults… This testing is just looking at the Inception mitigation overhead.
- safe RET no microcode – The purely kernel-based mitigation while using the prior Family 19h CPU microcode without the Inception mitigation there.
- safe RET – The default safe RET mode when using the newest CPU microcode.
- IBPB – The alternative IBPB-based mitigation approach.
Now let’s move on to the tests themselves:
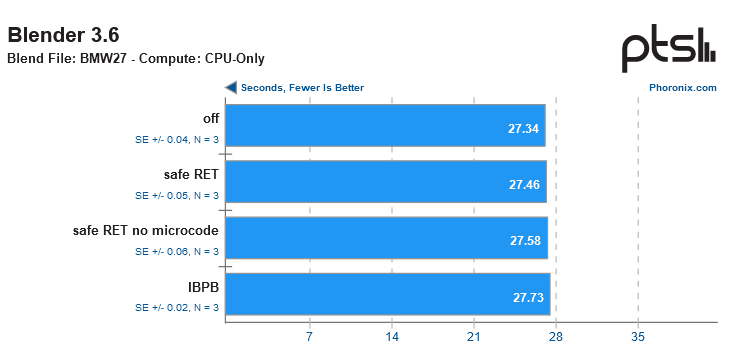
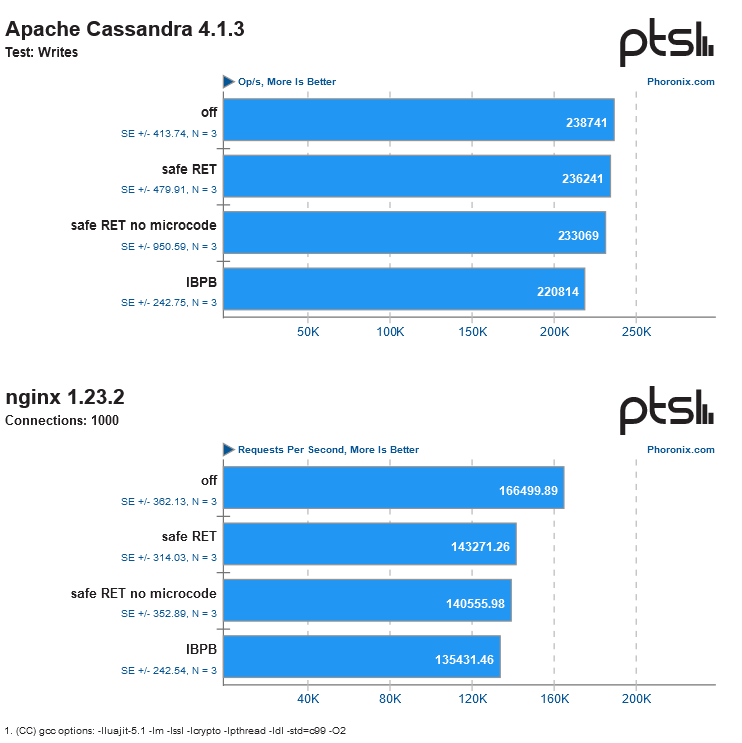
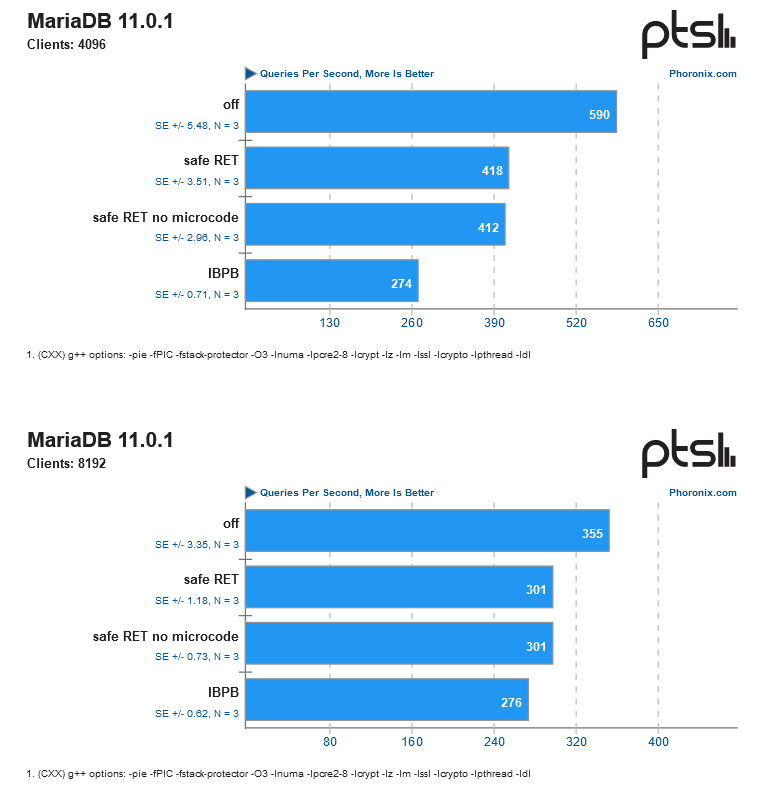
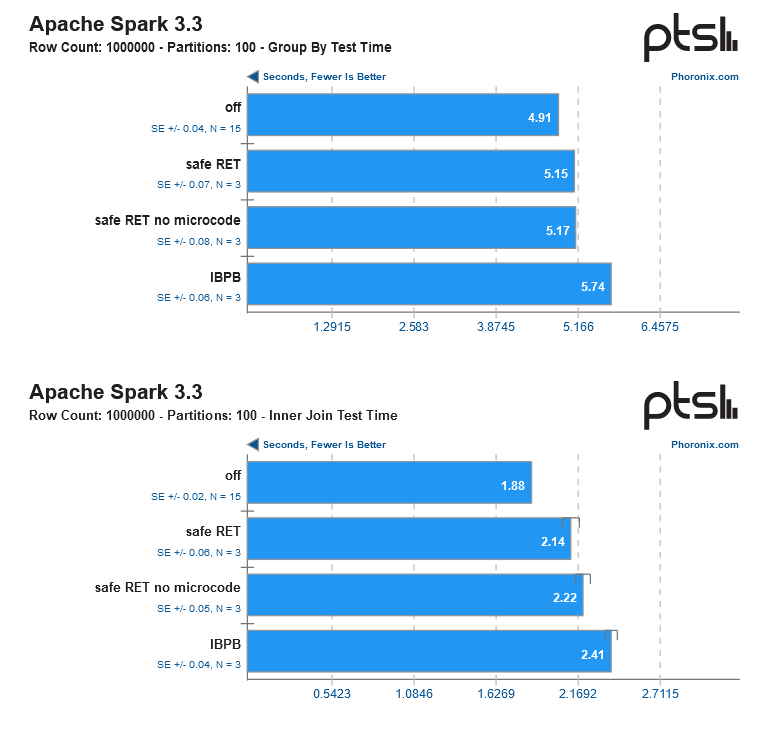
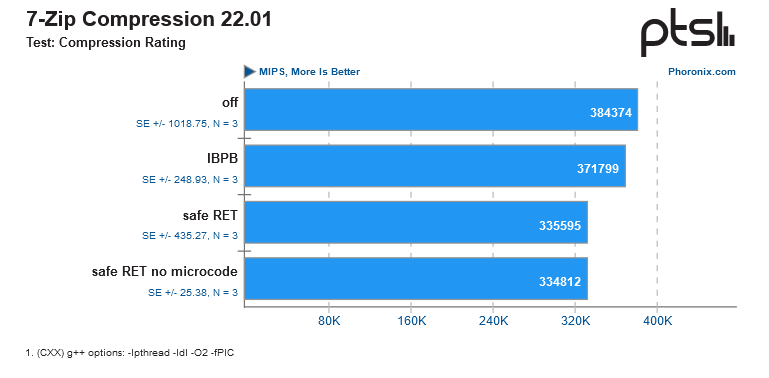
According to the research results, the main performance penalty fell on the server and near-server segment (intensive loads like databases and so on), while ordinary users will either not feel the decrease in their CPU speed at all (in games/rendering/Internet browsers), or (as in the case of 7-zip) will lose about 10-15% of performance.
In summary: if you are an ordinary user or a gamer, you should not take this information too seriously, because such vulnerabilities exist in both Intel and AMD processors and the fight against them is commonplace for semiconductor giants.
Source: phoronix




